Back
How to Spot a Phishing Email Attempt
- By Elite CIO
 Jan 30, 2025
Jan 30, 2025 11
11
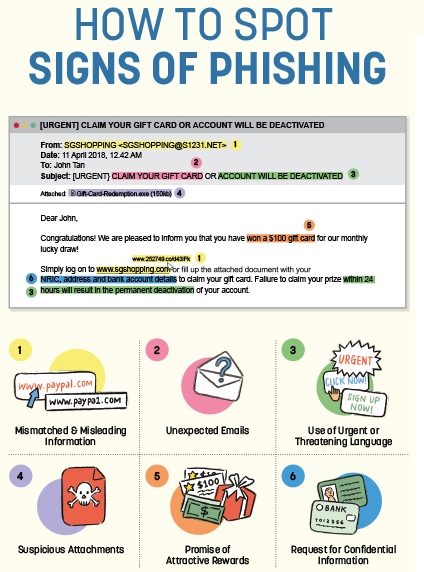 How to Spot a Phishing Email Attempt
How to Spot a Phishing Email Attempt
Phishing attacks are one of the most common types of data breach attempts, with 3.4 billion phishing emails being sent every single day, according to Splunk. Furthermore, 80% of organizations globally have reported phishing attempts that target their employees, proving just how widespread these attacks are. The rise of ChatGPT and similar generative AI tools has made it even easier for bad actors to create legitimate-looking phishing messages in a fraction of the time, further increasing the risk of phishing attacks.
🚨 Nine Warning Signs of a Phishing Attack – Stay Cyber-Safe! 🚨
Following warning signs of a phishing attack that every single person needs to know in order to identify one, both at work and at home.
🔍 1. Urgent or Threatening Requests
By pressuring you to reply quickly or issuing ultimatums, criminals hope to instil panic and fear to trick you into providing confidential information. Be wary of emails with phrases such as ‘urgent action required’ or ‘your account will be terminated’. If you have good reason to believe it is a scam, delete the message immediately.
📌 Example: “Your account will be locked in 24 hours! Click here to verify.”
✅ Red Flag: Cybercriminals use urgency to pressure you into acting without thinking.
📩 2. Suspicious Sender Email
Cyber criminals often test their luck by sending mass emails to large groups of people, in hopes that someone responds. If you receive an email about an invoice for an item you did not purchase, do not click on the links and attachments and delete the email immediately.
📌 Example: Email from "IT-Support@yourcompany.co" instead of "IT-Support@yourcompany.com"
✅ Red Flag: Look for subtle changes in domain names or misspelled company names.
🏷️ 3. Generic Greetings & Lack of Personalization
📌 Example: “Dear User” or “Dear Valued Customer” instead of your actual name.
✅ Red Flag: Legitimate companies usually personalize communications.
📎 4. Unexpected Attachments or Links
Cyber criminals include attachments in their emails as a method to infect a user’s device with malware and steal their data. It may be instinctive to open attachments we receive but it is important to exercise caution. Look out for suspicious attachment names and file types. If the attachment is for something you have no recollection of or uses an uncommon file type such as .exe, trash it.
📌 Example: An invoice or security update attachment you weren’t expecting.
✅ Red Flag: Attachments may contain malware, and links can redirect to fake login pages.
✍️ 5. Poor Grammar & Spelling Mistakes
📌 Example: “Pleese reset yore password immediately to secure your acount.”
✅ Red Flag: Official communications are typically well-written and professional.
🔗 6. Suspicious Links & Fake URLs
📌 Example: Hovering over "Click Here" reveals a link leading to "login-update-secure.com" instead of "yourcompany.com".
✅ Red Flag: Always hover over links before clicking.
🔑 7. Requests for Sensitive Information
Most organisations will never ask for your personal information such as NRIC, login credentials and credit card details to be sent over the Internet. If the sender claims to be from your bank and requests for your bank account number, it should raise a red flag immediately. When in doubt, contact the company directly to clarify, but be sure not to use the contact information provided in the email.
📌 Example: “Please confirm your username and password to avoid suspension.”
✅ Red Flag: Legitimate IT teams never ask for passwords via email.
🏢 8. Fake Branding & Logos
📌 Example: Company logos that look pixelated, stretched, or slightly altered.
✅ Red Flag: Cybercriminals often use low-quality branding to trick users.
🎁 9. Too-Good-to-Be-True Offers
False offers of amazing deals or unbelievable prizes are commonly used by cyber criminals to encourage you to act immediately. If you all you need to do is to click on a pop-up or complete an email survey to win a free trip to Europe, it is safe to presume that it is a phishing scam. Remember the old adage, ‘If it sounds too good to be true, it probably is’.
📌 Example: “Congratulations! You’ve won an all-expenses-paid trip—just enter your company email to claim.”
✅ Red Flag: Scammers exploit curiosity to trick users into clicking.
🚀 How to Stay Safe?
✔️ Think Before You Click – Verify links before clicking.
✔️ Report Suspicious Emails – Forward to IT Security Team instead of responding.
✔️ Enable Multi-Factor Authentication (MFA) – Adds an extra layer of security.
✔️ Use Company-Vetted Tools – Access corporate platforms through official channels only.
🚨 Report Phishing Attempts to [security@yourcompany.com] or your IT department immediately.